Due to the increased number of business services on open networks and distributed platforms, security has become a critical issue. Developers must support software with security measures. To utilize practices and experiments on secure software analysis, design, implementation and testing, we are conducting researches on security patterns, such as application and verification of patterns.
Taxonomy and Survey on Security Pattern Research
Security patterns encompass security-related issues in secure software system development and operations that often appear in certain contexts. Since the late 1990s about 500 security patterns have been proposed. Although the technical components are well investigated, the direction, overall picture, and barriers to implementation are not. Here, a systematic literature review of 240 papers is used to devise a taxonomy for security pattern research. Our taxonomy and the survey results should improve communications among practitioners and researchers, standardize the terminology, and increase the effectiveness of security patterns.
- List of papers reviewed: Information-SLR-Security-Pattern-Research-Details
- List of additional latest papers: Information-SLR-Additional-List
- Hironori Washizaki, Tian Xia, Natsumi Kamata, Yoshiaki Fukazawa, Hideyuki Kanuka, Dan Yamaoto, Masayuki Yoshino, Takao Okubo, Shinpei Ogata, Haruhiko Kaiya, Takehisa Kato, Atsuo Hazeyama, Takafumi Tanaka, Nobukazu Yoshioka, G Priyalakshmi, “Taxonomy and Literature Survey of Security Pattern Research,” IEEE Conference on Applications, Information and Network Security (AINS), Langkawi, Malaysia, November 21-22, 2018
- Yurina Ito, Hironori Washizaki, Masatoshi Yoshizawa, Yoshiaki Fukazawa, Takao Okubo, Haruhiko Kaiya, Atsuo Hazeyama, Nobukazu Yoshioka, Eduardo B. Fernandez,“Systematic Mapping of Security Patterns Research,” Proceedings of the 22nd Conference on Pattern Languages of Programs Conference 2015 (PLoP 2015), October 24-26, Pittsburgh, Pennsylvania, USA.
Model-Driven Security Design Pattern Application
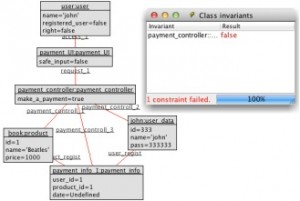
 The spread of software services through the Internet has increased the importance of software security. Security patterns is a tool that helps developers, architects and security specialists utilize security experts‟ knowledge and standardize how they respond to security threats. Security patterns contain recurring solutions about security problems. However, there is a possibility that developers may apply security patterns in inappropriate ways due to their lack of knowledge about dependencies among patterns. We propose an automated technique of applying security patterns in model-driven software development by defining model transformation rules that take into consideration pattern dependencies. Our technique prevents inappropriate applications such as applying security patterns to the wrong model elements or in the wrong order. We believe that our technique can help developers to apply security patterns to their own models automatically in appropriate ways.
The spread of software services through the Internet has increased the importance of software security. Security patterns is a tool that helps developers, architects and security specialists utilize security experts‟ knowledge and standardize how they respond to security threats. Security patterns contain recurring solutions about security problems. However, there is a possibility that developers may apply security patterns in inappropriate ways due to their lack of knowledge about dependencies among patterns. We propose an automated technique of applying security patterns in model-driven software development by defining model transformation rules that take into consideration pattern dependencies. Our technique prevents inappropriate applications such as applying security patterns to the wrong model elements or in the wrong order. We believe that our technique can help developers to apply security patterns to their own models automatically in appropriate ways.
- Yuki Shiroma, Hironori Washizaki, Yoshiaki Fukazawa, Atsuto Kubo, Nobukazu Yoshioka, Eduardo B. Fernandez, “Model-Driven Security Patterns Application and Validation,” 17th Conference on Pattern Languages of Programs (PLoP 2010), 2010.(PDF)
Validating Security Design Pattern Applications
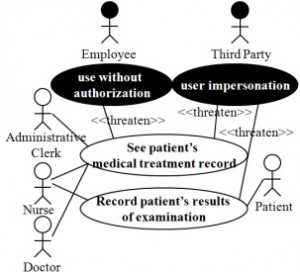
 Software developers are not necessarily security specialists, security patterns provide developers with the knowledge of security specialists. Although security patterns are reusable and include security knowledge, it is possible to inappropriately apply a security pattern or that a properly applied pattern does not mitigate threats and vulnerabilities. Herein we propose a method to validate security pattern applications. Our method provides extended security patterns, which include requirement- and design-level patterns as well as a new model testing process using these patterns. Developers specify the threats and vulnerabilities in the target system during an early stage of development, and then our method validates whether the security patterns are properly applied and assesses whether these vulnerabilities are resolved.
Software developers are not necessarily security specialists, security patterns provide developers with the knowledge of security specialists. Although security patterns are reusable and include security knowledge, it is possible to inappropriately apply a security pattern or that a properly applied pattern does not mitigate threats and vulnerabilities. Herein we propose a method to validate security pattern applications. Our method provides extended security patterns, which include requirement- and design-level patterns as well as a new model testing process using these patterns. Developers specify the threats and vulnerabilities in the target system during an early stage of development, and then our method validates whether the security patterns are properly applied and assesses whether these vulnerabilities are resolved.
- Takanori Kobashi, Nobukazu Yoshioka, Haruhiko Kaiya, Hiroyoshi Washizaki, Yoshiaki Fukazawa, “Validating Security Design Pattern Applications Using Model Testing,” Proceedings of 8th International Conference on Availability, Reliability and Security (ARES2013), pp.XX-YY, University of Regensburg, Germany, September 2-6, 2013.(PDF)
- Masatoshi Yoshizawa, Takanori Kobashi, Hiroyoshi Washizaki, Yoshiaki Fukazawa, Takao Okubo, Haruhiko Kaiya and Nobukazu Yoshioka, “Verification of Implementing Security Design Patterns Using a Test Template,” Proceedings of 9th International Conference on Availability, Reliability and Security (ARES2014), pp.XX-YY, Fribourg, Switzerland, 8th-12th September 2014. (to appear)(Verification of Implementing Security Design Patterns Using a Test Template.pdf)
Survey on Security Patterns and Modeling
Security has become an important topic for many software systems. Security patterns are reusable solutions to security problems. Although many security patterns and techniques for using them have been proposed, it is still difficult to adapt security patterns to each phase of software development. The following paper provides a survey of approaches to security patterns. As a result of classifying these approaches, a direction for the integration and future research topics is illustrated.
Moreover we conducted a study to examine the extent to which constructs provided by security requirements engineering approaches can support the use of security patterns as part of the analysis of security problems.
- Nobukazu Yoshioka, Hironori Washizaki, Katsuhisa Maruyama, “A Survey on Security Patterns,” Progress in Informatics, No.5, pp.33-47, 2008.
- A. Nhlabatsi, A. Bandara, S. Hayashi, C.B. Haley, J. Jurjens, H. Kaiya, A. Kubo, R. Laney, H. Mouratidis, B. Nuseibeh, Y. Tahara, T.T. Tun, H. Washizaki, N. Yoshioka and Y. Yu, “Security Patterns: Comparing Modeling Approaches”, in “Software Engineering for Secure Systems”, pp75-111, IGI Global, 2010.(PDF)